
F5 warns of critical BIG-IP RCE bug allowing device takeover

F5 has issued a security advisory warning about a flaw that might allow unauthenticated attackers with community entry to execute arbitrary procedure commands, execute file actions, and disable providers on Major-IP.
The vulnerability is tracked as CVE-2022-1388 and has a CVSS v3 severity score of 9.8, categorized as essential. Its exploitation can probably lead up to a total method takeover.
In accordance to F5’s safety advisory, the flaw lies in the iControl Relaxation ingredient and enables a destructive actor to send undisclosed requests to bypass the iControl Rest authentication in Massive-IP.
Thanks to the severity of the vulnerability and the prevalent deployment of Major-IP merchandise in critical environments, CISA (Cybersecurity and Infrastructure Safety Company) has also issued an notify today.
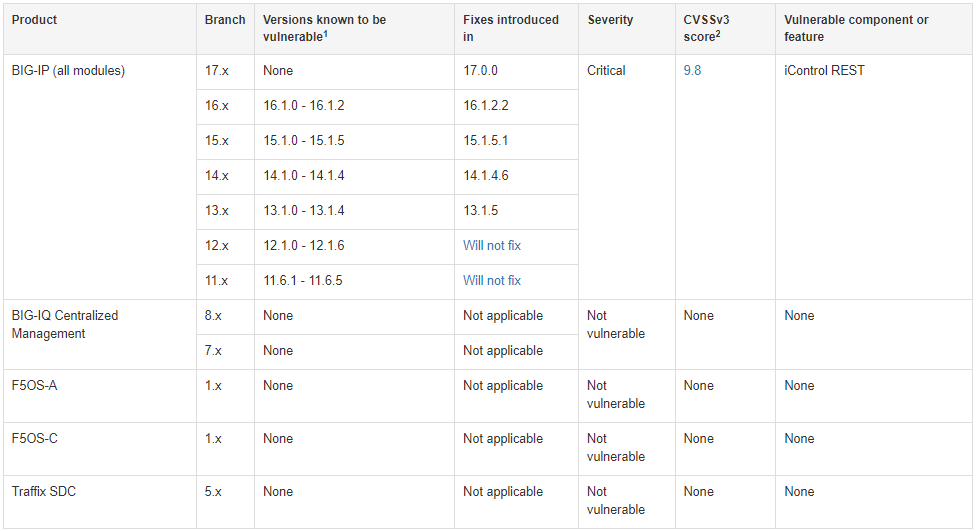
The complete list of the afflicted products and solutions is supplied beneath:
- Huge-IP versions 16.1. to 16.1.2
- Significant-IP versions 15.1. to 15.1.5
- Big-IP versions 14.1. to 14.1.4
- Big-IP variations 13.1. to 13.1.4
- Significant-IP versions 12.1. to 12.1.6
- Major-IP versions 11.6.1 to 11.6.5
F5 has released fixes in v17.., v16.1.2.2, v15.1.5.1, v14.1.4.6, and v13.1.5. The branches of 12.x and 11.x will not receive a fixing patch.
Also, the advisory clarifies that Huge-IQ Centralized Administration, F5OS-A, F5OS-C, and Targeted traffic SDC are not impacted by CVE-2022-1388.
F5 has provided the subsequent three productive mitigations that may perhaps be used temporarily for people who cannot implement the stability updates instantly.
Block all accessibility to the iControl Relaxation interface of your Huge-IP procedure as a result of self IP addresses, prohibit obtain only to dependable buyers and units via the administration interface, or modify the Big-IP httpd configuration.
F5 has presented all the facts on how to do the above in the advisory, but some techniques like blocking access fully could influence expert services, including breaking higher availability (HA) configurations. As this sort of, applying the stability updates is nevertheless the proposed pathway to observe, if doable.
Finally, F5 has unveiled a extra generic advisory to go over an extra established of 17 significant-severity vulnerabilities found out and fixed in Major-IP, so make absolutely sure to check out that one as well.
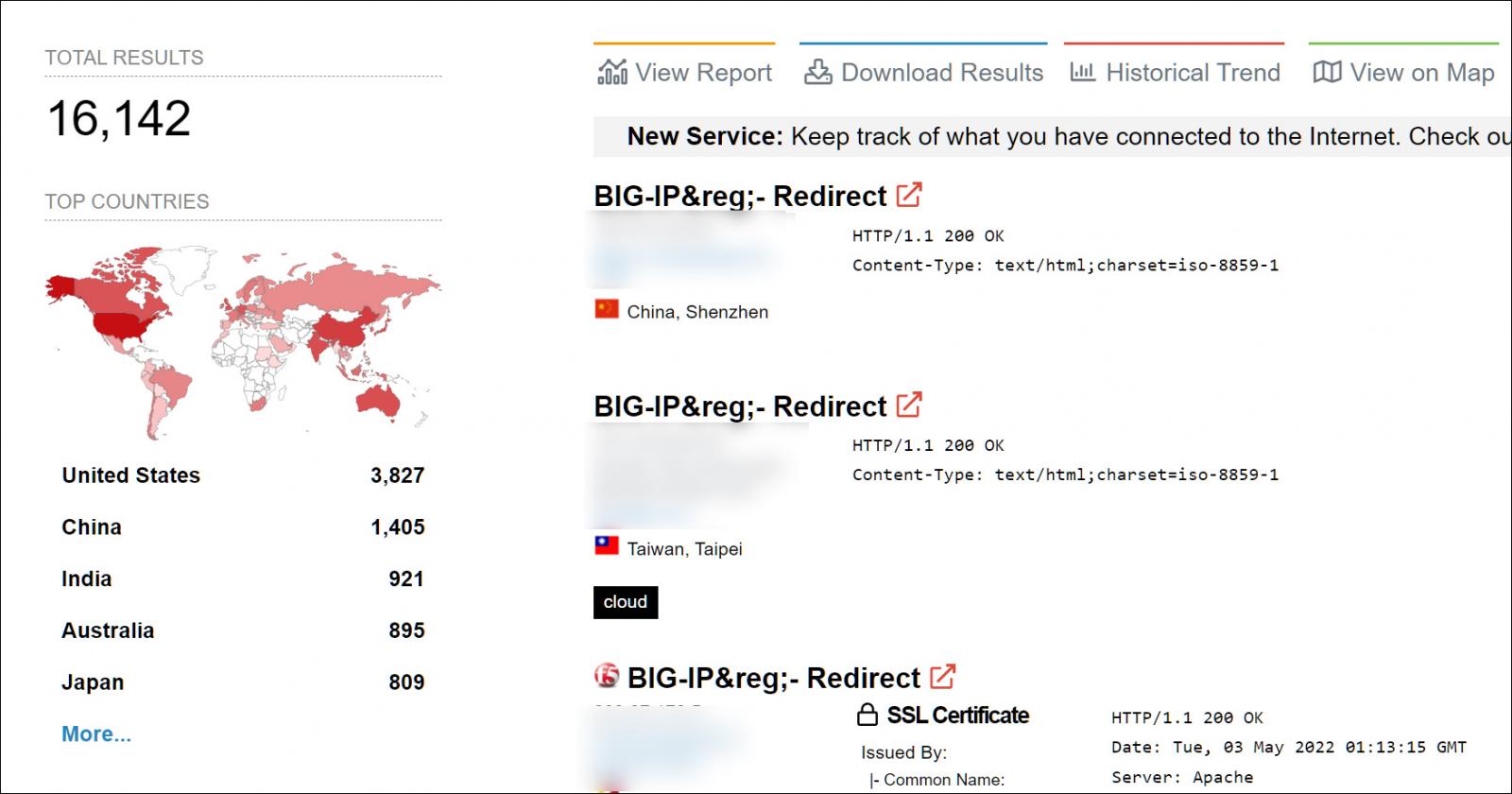
Around 16,000 Large-IP equipment uncovered
With F5 Huge-IP gadgets typically employed in the organization, this vulnerability offers a sizeable possibility for permitting danger actors to attain original access to company networks.
To make issues even worse, as an alternative of the business properly securing Large-IP equipment, security researcher Nate Warfield has noticed the total of publicly exposed devices significantly boost considering that 2020.
https://t.co/80tShneNwK – When CVE-2020-5902 dropped there have been ~10k F5 administration interfaces exposed on the web.
Right now there are 16k (https://t.co/2JPkVZwH5X is the @shodanhq query I use)
The pattern information from Shodan would suggest no person realized to lock these factors down pic.twitter.com/yC1oEbEZk9
— Nate Warfield | #StandWithUkraine (@n0x08) May possibly 4, 2022
Making use of the question shared by Warfield, Shodan reveals that there are currently 16,142 F5 Major-IP equipment publicly exposed to the World wide web. Most of these gadgets are situated in the United states, adopted by China, India, Australia, and Japan.
Security scientists have currently started narrowing down the area of the vulnerability, and it would not be stunning to see menace actors start off scanning for susceptible units shortly.
For that reason, community admins have to patch these equipment as shortly as probable or at least utilize the supplied mitigations.
