
New Linux bug gives root on all major distros, exploit released

A new Linux vulnerability recognized as ‘Dirty Pipe’ will allow area buyers to get root privileges as a result of publicly obtainable exploits.
Now, stability researcher Max Kellermann responsibly disclosed the ‘Dirty Pipe’ vulnerability and said that it has an effect on Linux Kernel 5.8 and afterwards versions, even on Android gadgets.
The vulnerability is tracked as CVE-2022-0847 and permits a non-privileged person to inject and overwrite data in go through-only files, like SUID procedures that operate as root.
Kellerman discovered the bug right after tracking down a bug that was corrupting internet server obtain logs for 1 of his prospects.
Kellerman states that the vulnerability is identical to the Dirty COW vulnerability (CVE-2016-5195) fixed in 2016.
Public exploits give root privileges
As portion of the Filthy Pipe disclosure, Kellerman produced a proof-of-notion (PoC) exploit that lets community users to inject their own facts into delicate study-only documents, getting rid of constraints or modifying configurations to offer bigger accessibility than they typically would have.
For illustration, security researcher Phith0n illustrated how they could use the exploit to modify the /and so on/passwd file so that the root consumer does not have a password. When this change is created, the non-privileged consumer could basically execute the ‘su root‘ command to achieve access to the root account.
Why did I overwrite the /etcetera/passwd?
Due to the fact this file will save all the person information and facts on Linux.
I eliminate the “x” flag driving the “root” user, it suggests that I established an empty password for this consumer. So I can use “su root” to escalate privilege devoid of qualifications.— Phith0n (@phithon_xg) March 7, 2022
Nonetheless, an updated exploit by safety researcher BLASTY was also publicly unveiled currently that will make it even easier to gain root privileges by patching the /usr/bin/su command to drop a root shell at /tmp/sh and then executing the script.
As soon as executed, the person gains root privileges, as shown by BleepingComputer underneath in Ubuntu 20.04.3 LTS operating the 5.13.-27-generic kernel.
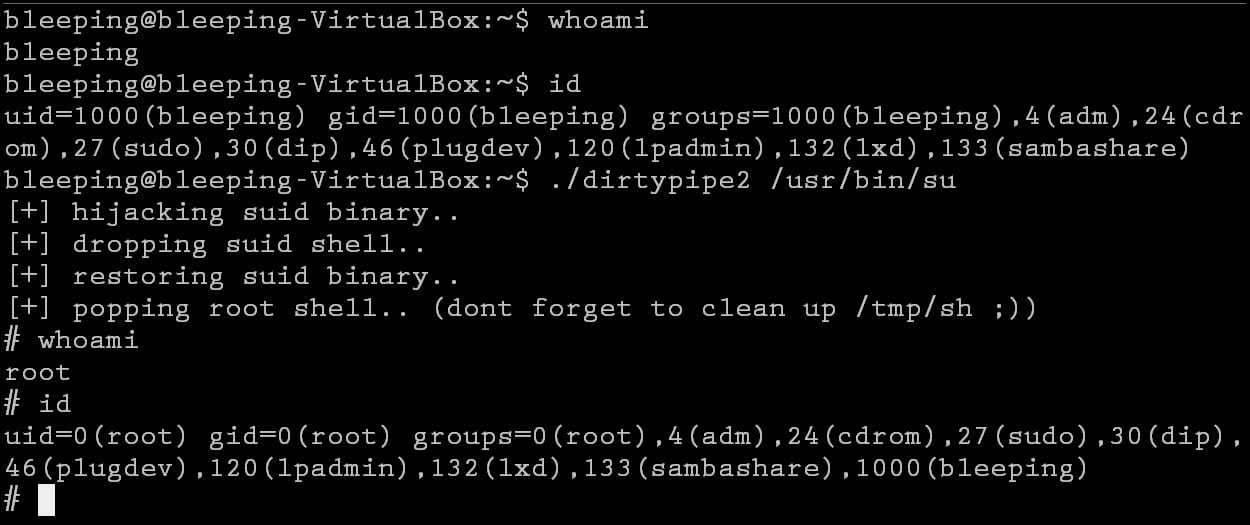
Source: BleepingComputer
The vulnerability was responsibly disclosed to numerous Linux maintainers starting up on February 20th, 2022, including the Linux kernel security team and the Android Safety Group.
Even though the bug has been fastened in Linux kernels 5.16.11, 5.15.25, and 5.10.102, many servers go on to operate out-of-date kernels building the launch of this exploit a substantial problem to server directors.
Additionally, due to the relieve of attaining root privileges working with these exploits, it is only a make a difference of time ahead of danger actors start using the vulnerability when conducting assaults. The identical Soiled COW vulnerability was beforehand made use of by malware, even although it was more challenging to exploit.
This bug is primarily about for world wide web internet hosting vendors who supply Linux shell accessibility or universities that commonly present shell access to multi-consumer Linux techniques.
It has been a rough twelve months for Linux, with many superior-profile privilege elevation vulnerabilities disclosed.
These contain privilege elevation vulnerabilities in the Linux iSCSI subsystem, another kernel bug, the Extended Berkeley Packet Filter (eBPF), and Polkit’s pkexec ingredient.
