New data-wiping malware used in destructive attacks on Ukraine

Cybersecurity firms have identified a new info wiper utilized in destructive attacks currently against Ukrainian networks just as Russia moves troops into areas of Ukraine.
A knowledge wiper is malware that deliberately destroys data on a system to make the data unrecoverable and for the operating technique to no extended work correctly.
This morning, Ukrainian governing administration organizations and banking institutions were hit with DDoS attacks that took sites offline.
Shortly following, cybersecurity firms Symantec and ESET disclosed that they discovered a new harmful knowledge wiper malware also employed in cyberattacks today towards Ukrainian businesses.
Symantec shared the hash of the new info-wiper on Twitter, which is presently remaining detected by only 16/70 protection engines on VirusTotal.
“According to Symantec Menace Hunter telemetry, they have discovered new wiper attacks in Ukraine, Latvia, and Lithuania. Targets have provided finance and federal government contractors,” Vikram Thakur, Technical Director at Symantec Risk Intelligence, shared in a assertion to BleepingComputer.
ESET also posted a in-depth Twitter thread containing a technological analysis of the new details wiper and how they have viewed it deployed.
According to ESET, the new data wiper is detected as Get32/KillDisk.NCV and was viewed deployed on hundreds of gadgets on Ukrainian networks now.
Though the cyberattacks happened now, ESET notes that the malware was compiled on 12/28/21, indicating that the assaults may possibly have been prepared for some time.
“The PE compilation timestamp of one particular of the sample is 2021-12-28, suggesting that the assault may possibly have been in planning for pretty much two months,” tweeted ESET.
From an assessment of the malware by BleepingComputer, the wiper incorporates 4 embedded drivers named DRV_X64, DRV_X86, DRV_XP_X64, and DRV_XP_X86, as revealed under.
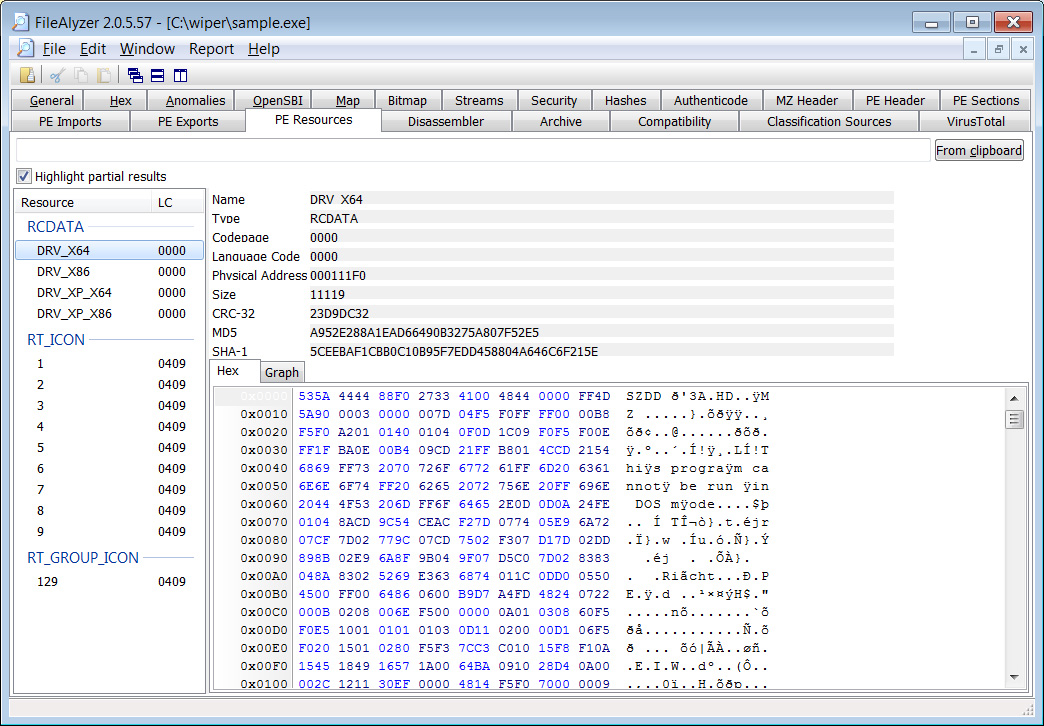
Supply: BleepingComputer
These drivers are compressed making use of the Home windows ‘compress’ command but after expanded, they are signed by ‘CHENGDU YIWO Tech Advancement Co., Ltd.,’ the proprietors of the EASUS details recovery and disk management software builders.
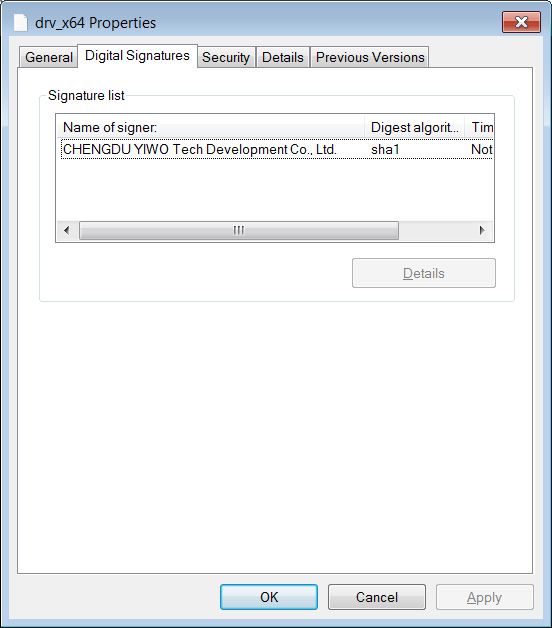
Supply: BleepingComputer
When the malware is executed, the wiper will put in one of these drivers as a new Windows services.
Source: BleepingComputer
Strings inside of the drivers indicate that they belong to the EASUS Partition Manager system.
Disk
DeviceHarddisk{f5ac61d6de3ce41dbc84aacfdb352f5c66627c6ee4a1c88b0642321258bd5462}uPartition0
DeviceEPMNTDRV
DosDevicesEPMNTDRVESET thinks that these EASUS motorists have been coopted to corrupt the device’s information ahead of the malware reboots the laptop.
Stability researcher Silas Cutler has confirmed that the info wiper will also trash the device’s Learn Boot Record, producing the system unbootable.
ESET warned that in at the very least one particular of these attacks, it was not focused at specific computer systems and was deployed right from the Home windows domain controller.
This signifies that the risk actors experienced obtain to these networks for some time.
“In 1 of the specific corporations, the wiper was dropped through the default (domain plan) GPO meaning that attackers experienced probable taken command of the Energetic Listing server,” clarifies ESET.
For those people fascinated in more specialized specifics, you can comply with SentinelOne researcher J. A. Guerrero-Saade’s analysis on Twitter.
Second wiper utilised in assaults on Ukraine
This data-wiper is the second one particular utilized against Ukrainian networks in the very last two months.
In January, Microsoft disclosed that a damaging knowledge-wiping malware disguised as ransomware was made use of in attacks versus various Ukrainian corporations.
The January information-wiper was dubbed ‘WhisperGate’ and impersonated a ransomware assault, even focusing on distinct file extensions and dropping a ransom take note.
Even so, this malware was essentially a destructive details wiper that corrupts information and wipes the device’s Grasp Increase File, making it unachievable to boot into Windows or obtain information.
Whilst the assaults have not been attributed to Russia, data wipers have been a software employed by Russian point out-sponsored danger actors in the earlier.
A info-wiping attack was performed in 2017 when danger actors focused hundreds of Ukrainian businesses with the NotPetya ransomware.
In 2020, the USA formally indicted Russian GRU hackers believed to be section of the elite Russian hacking group recognized as “Sandworm” for the NotPetya attacks.
Update 2/23/22 10:04 PM EST: Additional assertion from Symantec.