
Microsoft Exchange servers hacked to deploy Cuba ransomware

The Cuba ransomware procedure is exploiting Microsoft Exchange vulnerabilities to gain initial access to corporate networks and encrypt equipment.
Cybersecurity company Mandiant tracks the ransomware gang as UNC2596 and the ransomware alone as COLDDRAW. Nevertheless, the ransomware is more normally regarded as Cuba, which is how BleepingComputer will reference them in the course of this post.
Cuba is a ransomware operation that released at the end of 2019, and although they commenced slow, they began to decide up velocity in 2020 and 2021. This improve in activity led to the FBI issuing a Cuba ransomware advisory in December 2021, warning that the gang breached 49 essential infrastructure businesses in the U.S.
In a new report by Mandiant, scientists demonstrate that the Cuba procedure largely targets the United States, adopted by Canada.
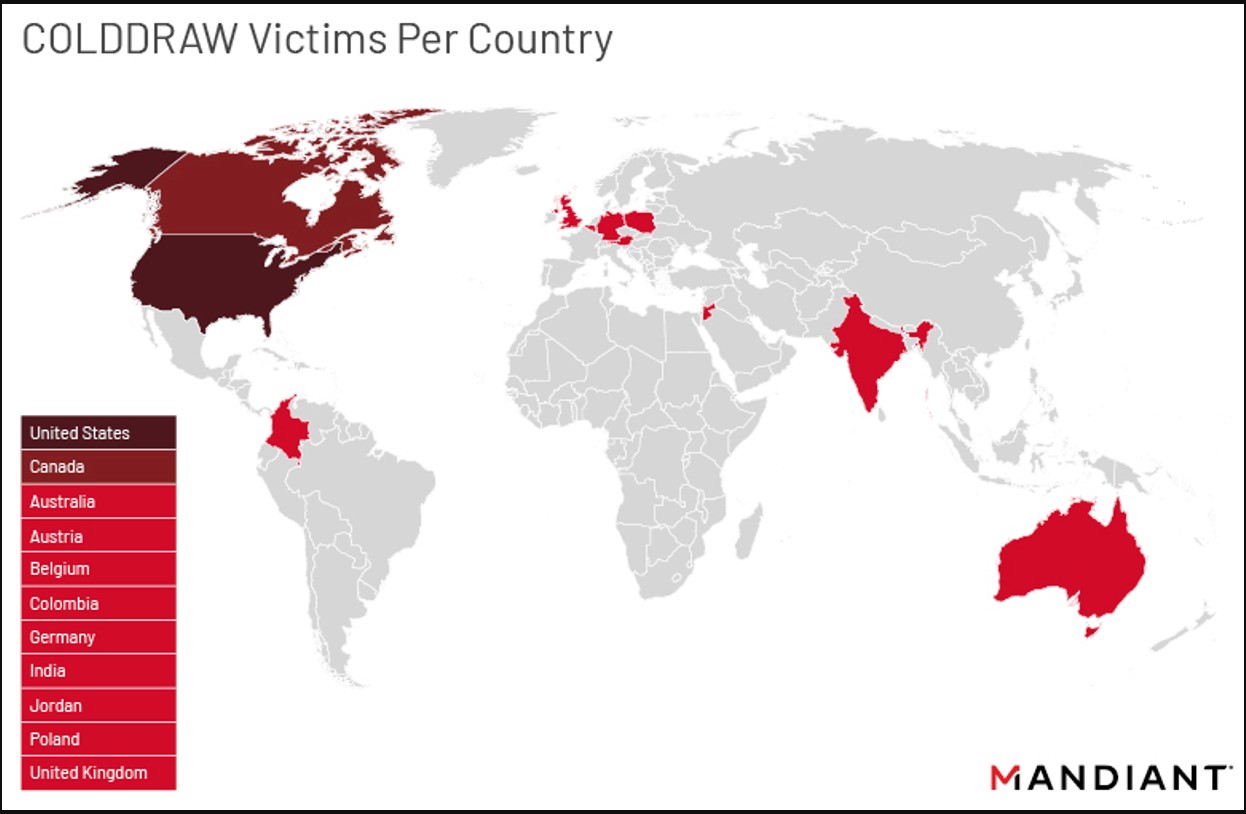
Supply: Mandiant
Mixing commodity and customized malware
The Cuba ransomware gang was found leveraging Microsoft Exchange vulnerabilities to deploy website shells, RATs, and backdoors to build their foothold on the concentrate on community because August 2021.
“Mandiant has also determined the exploitation of Microsoft Trade vulnerabilities, which includes ProxyShell and ProxyLogon, as a different access stage leveraged by UNC2596 probable as early as August 2021,” points out Mandiant in a new report.
The planted backdoors consist of Cobalt Strike or the NetSupport Manager remote access device, but the group also takes advantage of their possess ‘Bughatch’, ‘Wedgecut’, and ‘eck.exe”, and Burntcigar’ tools.
Wedgecut comes in the type of an executable named “check.exe,” which is a reconnaissance resource that enumerates the Lively Directory via PowerShell.
Bughatch is a downloader that fetches PowerShell scripts and documents from the C&C server. To evade detection, it hundreds in memory from a distant URL.
Burntcigar is a utility that can terminate procedures at the kernel degree by exploiting a flaw in an Avast driver, which is included with the software for a “bring your very own vulnerable driver” assault.
Lastly, there is a memory-only dropper that fetches the higher than payloads and hundreds them, called Termite. However, this instrument has been noticed in campaigns of numerous risk groups, so it’s not made use of completely by the Cuba risk actors.
The threat actors escalate privileges utilizing stolen account credentials sourced by way of the easily out there Mimikatz and Wicker equipment.
Then they perform network reconnaissance with Wedgecut, and following, they move laterally with RDP, SMB, PsExec, and Cobalt Strike.
The subsequent deployment is Bughatch loaded by Termite, followed by Burntcigar, which lays the floor for details exfiltration and file encryption by deactivating security resources.
The Cuba gang does not use any cloud services for the exfiltration step but rather sends every little thing on to their have private infrastructure.
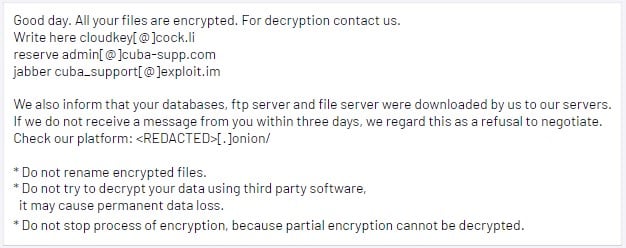
Source: Mandiant
An evolving procedure
Back again in May possibly 2021, Cuba ransomware partnered with the spam operators of the Hancitor malware to achieve obtain to company networks through DocuSign phishing e-mail.
Considering that then, Cuba has evolved its functions to target community-going through products and services vulnerabilities, this sort of as the Microsoft Exchange ProxyShell and ProxyLogon vulnerabilities.
This shift helps make the attacks far more strong but also easier to thwart, as stability updates that plug the exploited problems have been available for several months now.
The Cuba procedure will probably change its focus to other vulnerabilities at the time there are no much more useful targets jogging unpatched Microsoft Exchange servers.
This means that applying the out there safety updates as soon as the software package vendors release them is important in keeping a strong stability stance in opposition to even the most subtle menace actors.
