
Malware now using NVIDIA’s stolen code signing certificates

Menace actors are working with stolen NVIDIA code signing certificates to indicator malware to show up trusted and let malicious drivers to be loaded in Windows.
This week, NVIDIA confirmed that they endured a cyberattack that allowed menace actors to steal worker credentials and proprietary knowledge.
The extortion group, recognised as Lapsus$, states that they stole 1TB of data in the course of the assault and began leaking the info on-line following NVIDIA refused to negotiate with them.
The leak features two stolen code-signing certificates made use of by NVIDIA builders to indicator their drivers and executables.
As aspect of the #NvidiaLeaks, two code signing certificates have been compromised. Despite the fact that they have expired, Windows nevertheless permits them to be made use of for driver signing functions. See the speak I gave at BH/DC for additional context on leaked certificates: https://t.co/UWu3AzHc66 pic.twitter.com/gCrol0BxHd
— Bill Demirkapi (@BillDemirkapi) March 3, 2022
A code-signing certification makes it possible for developers to digitally signal executables and motorists so that Home windows and conclusion-buyers can verify the file’s operator and whether they have been tampered with by a third party.
To improve protection in Home windows, Microsoft also calls for kernel-method motorists to be code signed before the running method will load them.
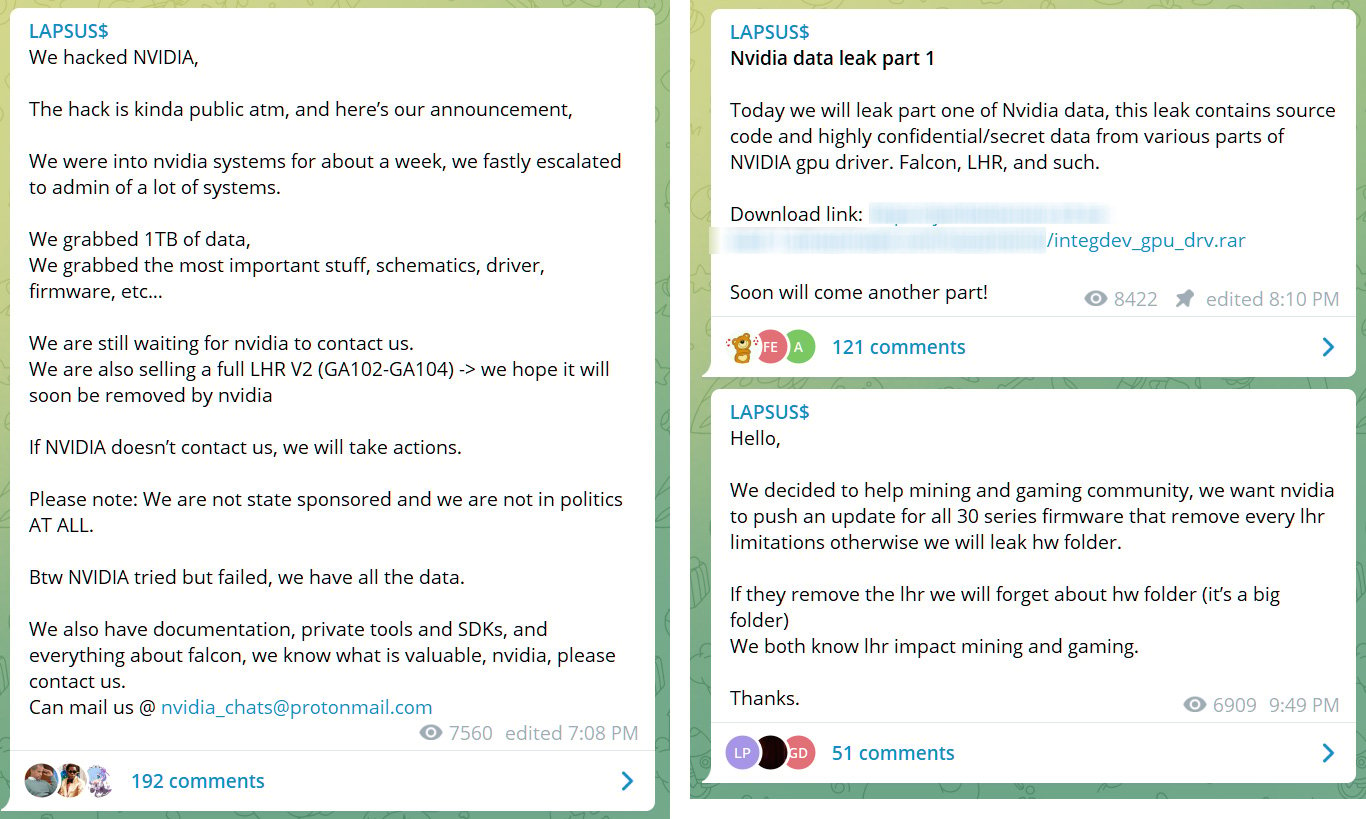
NVIDIA certificates utilised to indication malware
Immediately after Lapsus$ leaked NVIDIA’s code-signing certificates, safety scientists speedily observed that the certificates were being utilised to indication malware and other tools utilized by danger actors.
According to samples uploaded to the VirusTotal malware scanning provider, the stolen certificates ended up utilised to sign various malware and hacking applications, such as Cobalt Strike beacons, Mimikatz, backdoors, and distant access trojans.
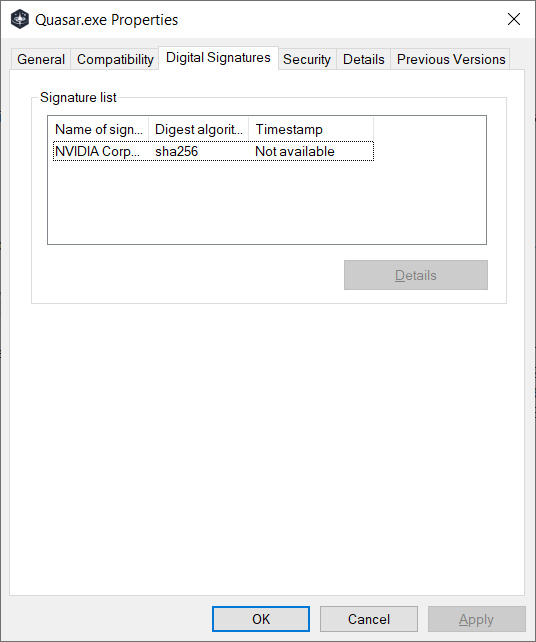
For case in point, a single threat actor made use of the certificate to signal a Quasar remote access trojan [VirusTotal], when a person else made use of the certificate to indicator a Windows driver [VirusTotal].
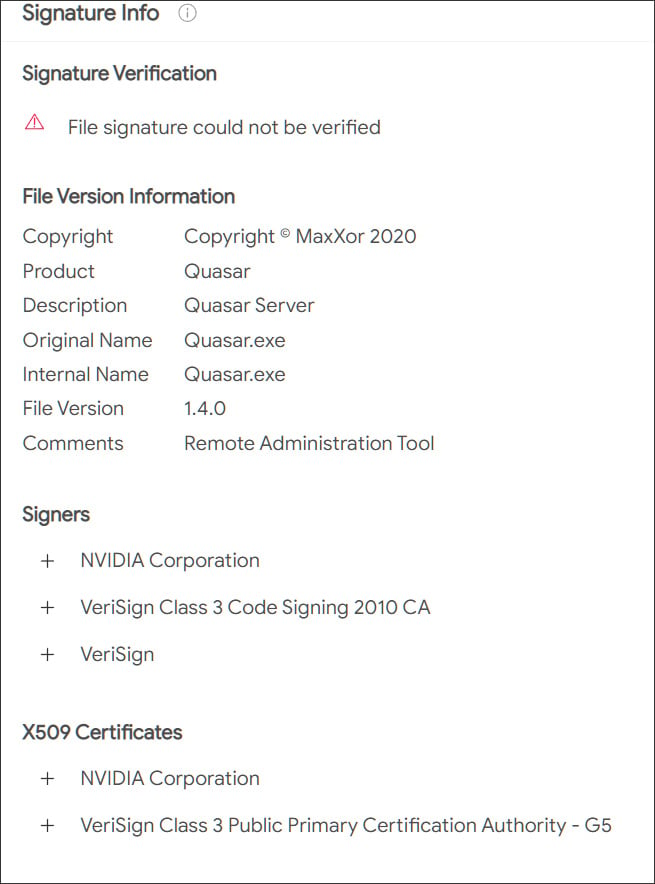
Security researchers Kevin Beaumont and Will Dormann shared that the stolen certificates make the most of the following serial quantities:
43BB437D609866286DD839E1D00309F5
14781bc862e8dc503a559346f5dcc518Some of the files ended up most likely uploaded to VirusTotal by stability researchers but others surface to be applied by risk actors for malware strategies [1, 2].
Though both stolen NVIDIA certificates are expired, Windows will nevertheless let a driver signed with the certificates to be loaded in the running procedure.
For that reason, applying these stolen certificates, danger actors get the edge of building their programs search like reputable NVIDIA plans and enabling destructive drivers to be loaded by Windows.
To protect against regarded vulnerable drivers from staying loaded in Windows, David Weston, director of business and OS security at Microsoft, tweeted that admins can configure Home windows Defender Application Command guidelines to manage what NVIDIA drivers can be loaded.
WDAC procedures operate on both equally 10-11 with no hardware requirements down to the household SKU inspite of some FUD misinformation i have witnessed so it should be your 1st selection. Develop a coverage with the Wizard and then insert a deny rule or enable certain variations of Nvidia if you need to have
— David Weston (DWIZZZLE) (@dwizzzleMSFT) March 3, 2022
However, using WDAC is not an straightforward task, specifically for non-IT Home windows consumers.
Due to the likely for abuse, it is hoped that the stolen certificates will be included to Microsoft’s certification revocation record in the long term to stop destructive drivers from loading in Home windows.
On the other hand, carrying out so will lead to reputable NVIDIA motorists to be blocked as nicely, so we will probable not see this occurring quickly.
