
Hive ransomware ports its Linux VMware ESXi encryptor to Rust

The Hive ransomware operation has transformed their VMware ESXi Linux encryptor to the Rust programming language and added new options to make it tougher for security scientists to snoop on victim’s ransom negotiations.
As the organization gets significantly reliant on digital equipment to conserve laptop or computer sources, consolidate servers, and for easier backups, ransomware gangs are making committed encryptors that focus on these providers.
Ransomware gang’s Linux encryptors commonly target the VMware ESXI virtualization platforms as they are the most typically used in the company.
Even though Hive has been making use of a Linux encryptor to target VMware ESXi servers for some time, a the latest sample reveals that they up-to-date their encryptor with characteristics initially released by the BlackCat/ALPHV ransomware operation.
Hive borrows capabilities from BlackCat
When ransomware operations assault a target, they try to conduct their negotiations in personal, telling victims if a ransom is not paid their facts will be printed and they will endure a reputational hit.
Having said that, when ransomware samples are uploaded to community malware assessment expert services, they are typically discovered by security researchers who can extract the ransom be aware and snoop on negotiations.
In many scenarios, these negotiations are then publicized on Twitter and somewhere else, resulting in negotiations to fall short.
The BlackCat ransomware gang eliminated Tor negotiation URLs from their encryptor to stop this from occurring. In its place, it required the URL to be handed as a command-line argument when the encryptor is executed.
This function stops scientists who find the sample from retrieving the URL as it’s not involved in the executable and only passed to the executable at operate time.
Although the Hive Ransomware now necessitates a login identify and password to entry a victim’s Tor negotiation webpage, these qualifications ended up formerly stored in encryptor executable, creating them straightforward to retrieve.
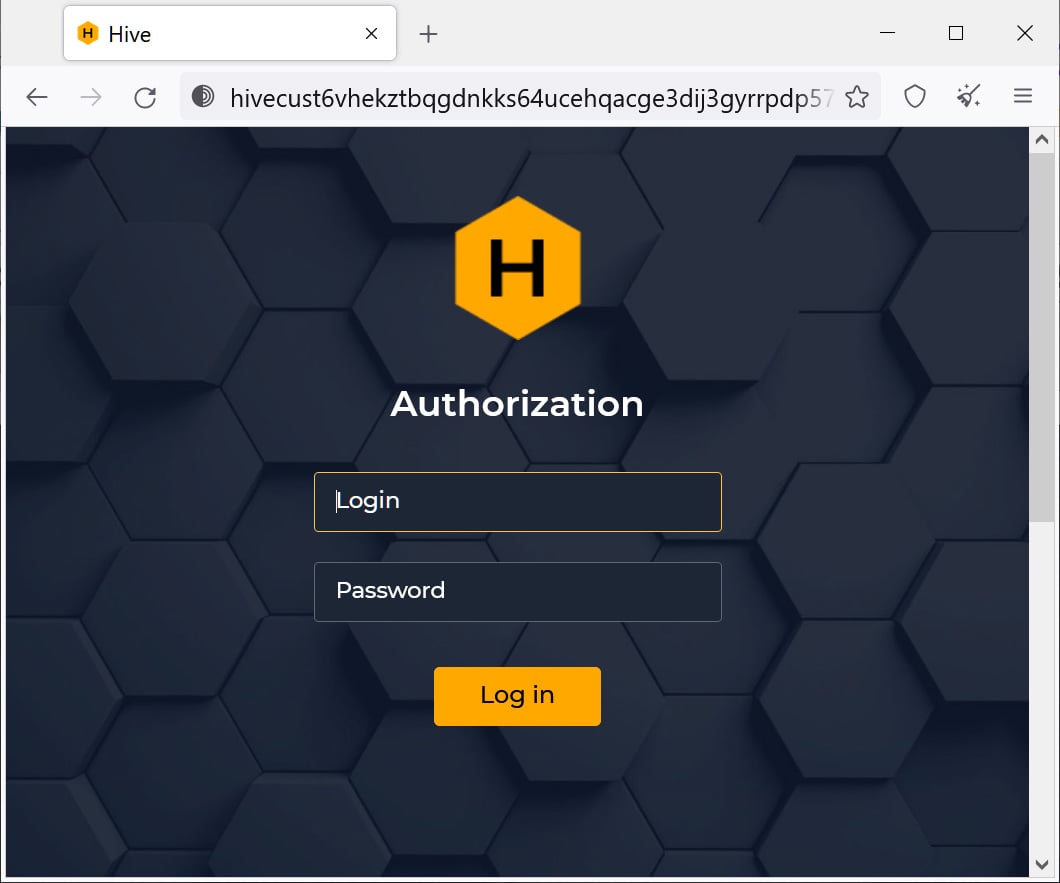
In a new Hive Linux encryptor found by Group-IB stability researcher rivitna, the Hive procedure now demands the attacker to offer the user name and login password as a command-line argument when launching the malware.

Source: rivitna
By copying BlackCat’s methods, the Hive ransomware operation has made it unattainable to retrieve negotiation login credentials from Linux malware samples, with the credentials now only obtainable in ransom notes produced for the duration of the attack.
It is not acknowledged if the Hive Home windows encryptors are also using this new command-line argument at this time, but if not, we will possible see it included shortly.
Rivitna also informed BleepingComputer that Hive continued to copy BlackCat by porting their Linux encryptor from Golang to the Rust programming language to make the ransomware samples extra economical and tougher to reverse engineer.
“Rust makes it possible for to get safer, quick, and economical code, when code optimization complicates assessment of Rust plan,” rivitna explained to BleepingComputer in a chat on Twitter.
With the encryption of VMware ESXi digital machines a essential part of a thriving assault, ransomware functions are constantly evolving their code to not only be a lot more effective, but to maintain the operations and negotiations magic formula.
As additional firms move to virtualization for their servers, we will carry on to see ransomware developers not only emphasis on Windows equipment, but also create dedicated Linux encryptors focusing on ESXi.
Due to this, all protection professionals and community admins need to pay out near interest to their Linux servers to detect indicators of assaults.
