
Hackers slip into Microsoft Teams chats to distribute malware

Security scientists warn that some attackers are compromising Microsoft Teams accounts to slip into chats and distribute malicious executables to contributors in the dialogue.
A lot more than 270 million users are relying on Microsoft Teams each month, several of them trusting the platform implicitly, despite the absence of protections towards destructive documents.
Simple but effective system
Researchers at Avanan, a Look at Stage organization that secures cloud email and collaboration platforms, observed that hackers started to fall malicious executable data files in discussions on Microsoft Groups interaction system.
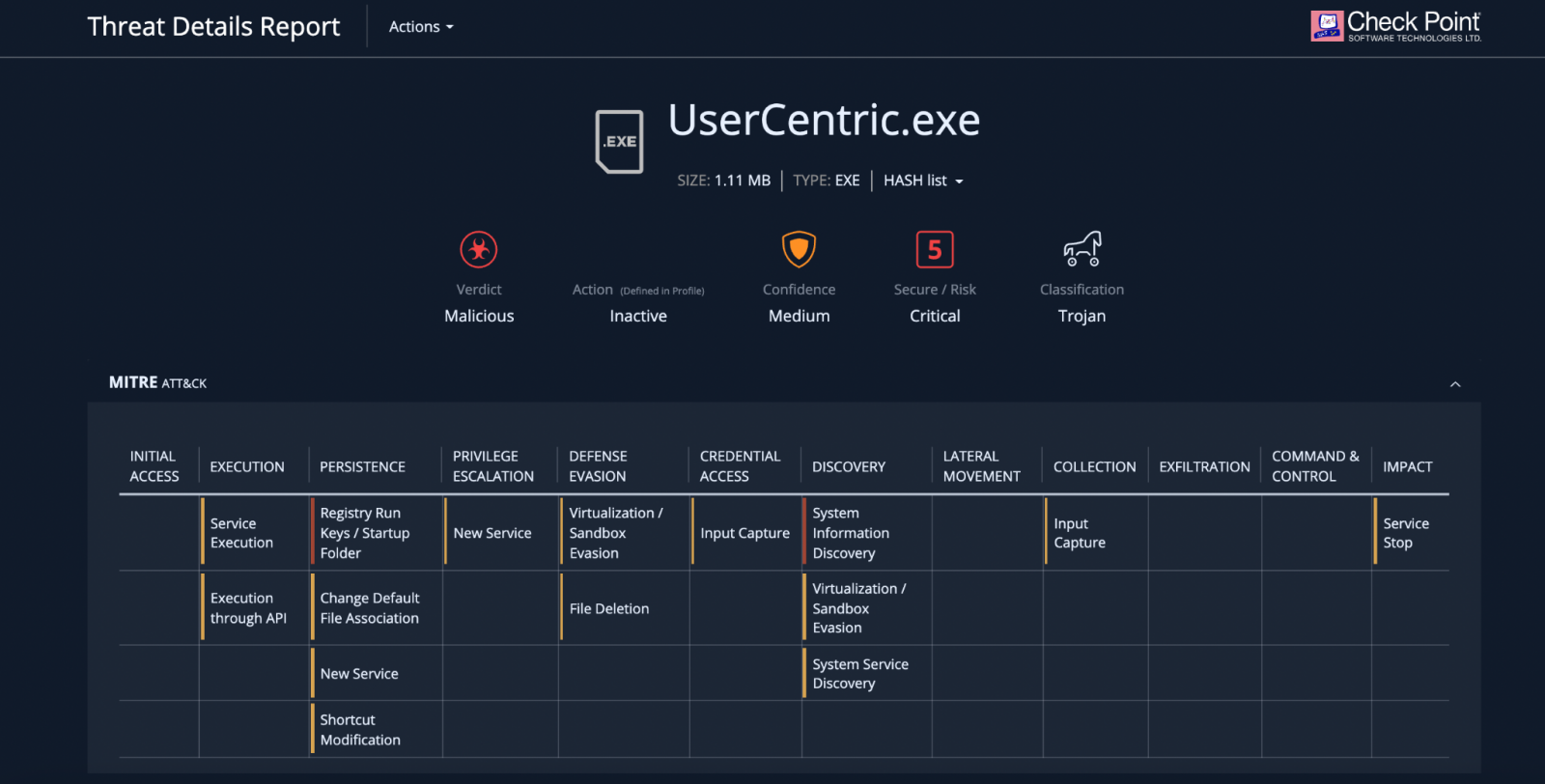
The assaults begun in January, the organization says in a report right now, and the danger actor inserts in a chat an executable file referred to as “User Centric” to trick the person into functioning it.
Once executed, the malware writes facts into the procedure registry installs DLLs and establishes persistence on the Home windows machine.
“In this Groups assault, hackers have hooked up a malicious Trojan doc to a chat thread. When clicked on, the file will finally just take around the user’s computer” – Avanan
The strategy utilised to obtain accessibility to Groups accounts remains unclear but some alternatives incorporate thieving qualifications for electronic mail or Microsoft 365 by means of phishing or compromising a spouse organization.
Computerized analysis of the malware dispersed this way reveals that the trojan can create persistence via Windows Registry Operate keys or by generating an entry in the startup folder.
It also collects in-depth facts about the running procedure and the components it runs on, together with the safety state of the machine dependent on the OS variation and the patches mounted.
Too much believe in
Whilst the attack is rather straightforward, it may perhaps also be pretty efficient for the reason that quite a few consumers have faith in information received about Teams, Avanan scientists say.
The company analyzed data from hospitals that use Groups and observed that doctors use the system to share clinical details unrestricted.
Though people today are normally suspicious of information received about electronic mail, because of to e mail phishing recognition training, they exhibit no warning with documents received around Groups.
Moreover, Groups provides guest and external accessibility capabilities that let collaboration with people outdoors the organization. Avanan claims that these invites are usually met by minimal oversight.
“Because of the unfamiliarity with the Groups platform, lots of will just rely on and approve the requests. Within just an firm, a consumer can pretty easily faux to be somebody else, regardless of whether it is really the CEO, CFO or IT help desk” – Avanan
The researchers say that the issue is aggravated by “the reality that default Teams protections are missing, as scanning for destructive links and files is limited” and “many e-mail protection methods do not present strong protection for Groups.”
To protect in opposition to this sort of attacks, Avanan endorses the next:
• Put into practice safety that downloads all information in a sandbox and inspects them for destructive content
• Deploy sturdy, complete-suite safety that secures all lines of enterprise communication, together with Groups
• Really encourage stop-end users to get to out to IT when viewing an unfamiliar file
