
Hackers breach MailChimp’s internal tools to target crypto customers

Email advertising agency MailChimp disclosed on Sunday that they had been strike by hackers who attained accessibility to inside customer support and account management equipment to steal audience facts and carry out phishing attacks.
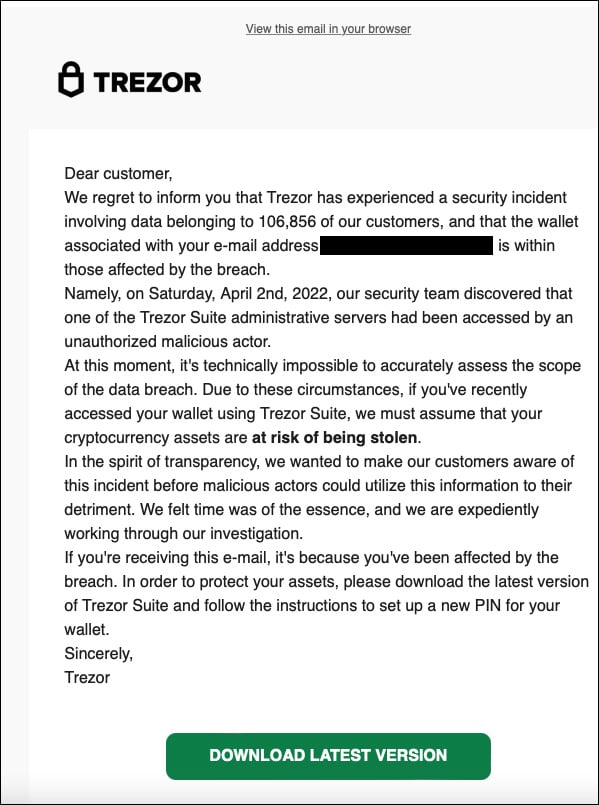
Sunday morning, Twitter was abuzz with stories from homeowners of Trezor hardware cryptocurrency wallets who obtained phishing notifications boasting that the organization experienced a details breach.
These emails prompted Trezort shoppers to reset their components wallet PINs by downloading destructive software that authorized thieving the stored cryptocurrency.
Resource: Twitter
Trezor later shared that MailChimp had been compromised by menace actors targeting the cryptocurrency industry, who performed the phishing attack.
MailChimp breach focused crypto, finance
In an e-mail to BleepingComputer, MailChimp has confirmed that the breach was extra significant than just Trezor’s account being accessed by threat actors.
In accordance to MailChimp, some of their staff fell for a social engineering attack that led to the theft of their qualifications.
“On March 26, our Stability workforce grew to become conscious of a destructive actor accessing one of our inner resources utilized by consumer-dealing with groups for shopper assist and account administration,” MailChimp CISO, Siobhan Smyth, informed BleepingComputer.
“The incident was propagated by an exterior actor who conducted a thriving social engineering attack on Mailchimp staff members, resulting in staff credentials remaining compromised.”
“We acted swiftly to tackle the situation by terminating entry for the compromised employee accounts and took steps to avert supplemental staff members from remaining influenced.”
These credentials were being utilised to obtain 319 MailChimp accounts and to export “audience facts,” most likely mailing lists, from 102 buyer accounts.
In addition to viewing accounts and exporting data, the menace actors gained accessibility to API keys for an undisclosed amount of consumers, which have now been disabled and can no extended be utilized.
Application Programming Interface (API) keys are accessibility tokens that allow MailChimp customers to handle their accounts and carry out promoting strategies specifically from their have sites or platforms.
Utilizing these compromised API keys, a menace actor can develop personalized e mail strategies, this sort of as phishing campaigns, and ship them to mailing lists with no accessing MailChimp’s consumer portal.
Smyth explained to BleepingComputer that all of the compromised account holders have been notified and that the risk actors accessed prospects in the cryptocurrency and finance sectors.
MailChimp states that they obtained reports of this accessibility staying utilised to perform phishing campaigns in opposition to stolen contacts but have not disclosed details about all those attacks..
MailChimp recommends that all shoppers help two-variable authentication on their accounts for even more security.
“We sincerely apologize to our people for this incident and realize that it delivers inconvenience and raises inquiries for our people and their shoppers. We consider delight in our protection tradition, infrastructure, and the believe in our prospects location in us to safeguard their facts. We’re self-assured in the stability measures and sturdy processes we have in position to secure our users’ info and protect against upcoming incidents.”
Siobhan Smyth, Mailchimp’s CISO.
This assault is reminiscent of recent breaches by the Lapsus$ hacking team, who used social engineering, malware, and credential theft to get obtain to various effectively-regarded providers, together with Nvidia, Samsung, Microsoft, and Okta.
The Okta breach was completed by a comparable method as MailChimp, by social-engineering a contractor who experienced entry to inner buyer assist and account management devices.
BleepingComputer has sent MailChimp and Trezor further more thoughts about the breach but has not heard back again.
