Google gives Android users an easy path to secure DNS
If you were being upset to hear that Android 13 wouldn’t assist DNS above HTTPS, I’ve obtained some fantastic information. It turns out that Google was not developing it into Android alone for the impending update due to the fact (as observed at the time) it could also basically be carried out through a separate Android Mainline/APEX module, and that is particularly what has transpired. Traveling in the facial area of “fragmentation,” Google just brought DNS about HTTPS to all Android 11 equipment and later on, and even some Android 10 products.
Google introduced the characteristic right now on its Stability Blog site, outlining the added benefits (if you weren’t by now knowledgeable of them) as nicely as the system for how the improve has rolled out. If you were not conscious of it, DNS in excess of HTTPS features some big positive aspects to your safety.
What is DNS over HTTPS?
Although you might currently be conscious of factors like HTTPS connections as getting a far more secure way to browse the world-wide-web (luckily, the default encounter pretty much all the time now), there is certainly actually nonetheless a gap in safety that transpires when you in fact navigate to a new site. See, when you take a look at a net tackle, you are not connecting to a string of words. That’s not a real handle, just an abstraction for the genuine location you want to link to — the “area name” is tied to an IP address.
Essentially, when you variety androidpolice.com into your deal with bar, you are hunting up that title in a type of cellular phone guide — which is the DNS method. And, it turns out, DNS queries aren’t actually completed in a secure system by default, exposing you to factors like man-in-the-middle assaults where by anyone can position you at the mistaken place when you ask for an deal with. There are means to plug the gaps in stability even with this fairly insecure question, but the system even now has a “bootstrapping trouble,” in which the chain of have faith in in any buy of functions turns into tough to create.
Creating these queries in an unencrypted way is also a privacy worry, as somebody in the right place could see which websites you happen to be viewing or perhaps even interfere with accessing sure ones. Don’t forget again when ISPs used to route domains that didn’t solve to their homepage or adverts? This really should avoid that, and it can also make a dent against regulatory makes an attempt to block targeted visitors to specific sources, like the British isles government’s repeated attempts to block adult information.
Android has previously supported a single strategy of working with DNS over TLS to repair this issue, allowing for you to have an encrypted query to a DNS server — and that suggests you can have confidence in the address that is offered when you question, assuming you have confidence in the server. That has some rewards and disadvantages. Some businesses like Cloudflare have argued that it is a little bit a lot less secure given that it won’t be able to completely disguise DNS queries as frequent HTTPS visitors. On prime of that, DNS around HTTPS provides overall performance enhancements and has presently been adopted by a great deal of DNS operators (like Cloudflare and Google). In accordance to Google’s John Wu (the developer initially at the rear of the well-known Magisk root option) the implementation below is even written in Rust — some thing both equally safety-aware programmers and Rust enthusiasts will dig.
Now right here for Android 11 and later
As mentioned, the aspect has been implemented as section of Android’s DNS Resolver module, and an update for it has rolled out as element of a the latest Google Perform system update. According to Google, suitable products ought to previously aid it. Even though this module was optional in Android 10, in accordance to Esper.io’s Mishaal Rahman, it turned necessary in Android 11, so all Google-certified Android 11 devices and later on that obtain Google Engage in system updates must be ready to use it, and some Android 10 equipment that applied the element when it was optional could also have it. In accordance to Rahman, it can be easy to test by managing “cmd product_config get netd_indigenous doh” in an ADB shell (no prices. If it returns “1,” you’ve got received DNS above HTTPS.
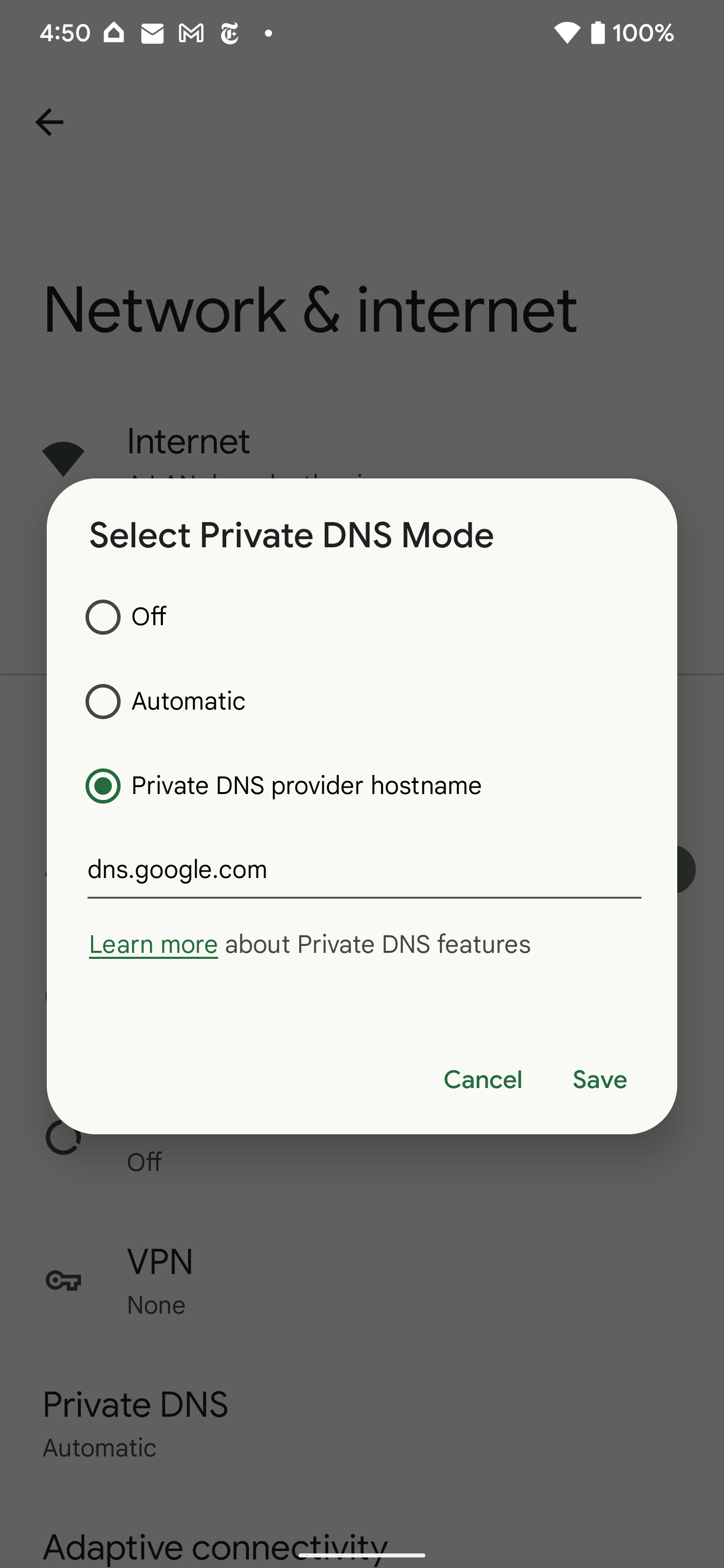
If all of this went in excess of your head, the quite short version is that Google was capable to give the probable huge bulk of Android units in the wild a element that will allow them use the web even more securely and securely. The aspect might not present lots of gains, though, if your DNS server isn’t suitable with DNS around HTTPS, but you can forcibly allow your Android gadget to hook up to a person by enabling the Protected Private DNS feature (search for “Non-public DNS” in Configurations) choosing “private DNS company name” and offering possibly Google or Cloudflare’s hostnames.
- Cloudflare: cloudflare-dns.com
- Google: dns.google
(If you attempt a more focused hostname like 1dot1dot1dot1.cloudflare-dns.com, that won’t work for some cause.)
At some point, this upgraded method should really just get the job done without the need of you obtaining to even be concerned about which DNS server you may well be using. For now, the function is ready it truly is on DNS suppliers to end rolling out support for DNS about HTTPS.