
Conti Ransomware source code leaked by Ukrainian researcher

A Ukrainian researcher proceeds to deal devastating blows to the Conti ransomware operation, leaking further internal conversations, as properly as the supply for their ransomware, administrative panels, and extra.
It has been very a damaging week for Conti right after they sided with Russia on the invasion of Ukraine and upset Ukrainian adverts (affiliates) and a researcher who has been secretly snooping on their procedure.
On Sunday, a Ukrainian researcher using the Twitter handle @ContiLeaks leaked 393 JSON files containing over 60,000 inside messages taken from the Conti and Ryuk ransomware gang’s private XMPP chat server.
These conversations were being from January 21st, 2021, by way of February 27th, 2022, giving a treasure trove of info on the cybercrime corporation, these kinds of as bitcoin addresses, how the gang is organized as a small business, evading regulation enforcement, how they conduct their assaults, and considerably much more.
On Monday, the researcher saved leaking a lot more damaging Conti details, which includes an supplemental 148 JSON data files made up of 107,000 internal messages because June 2020, which is all around when the Conti ransomware procedure was very first launched.
ContiLeaks began releasing more facts all through the night time, which include the supply code for the gang’s administrative panel, the BazarBackdoor API, screenshots of storage servers, and additional.
Nonetheless, a portion of the leak that received folks excited was a password-guarded archive containing the resource code for the Conti ransomware encryptor, decryptor, and builder.
When the leaker did not share the password publicly, yet another researcher soon cracked it, allowing anyone obtain to the supply code for the Conti ransomware malware data files.
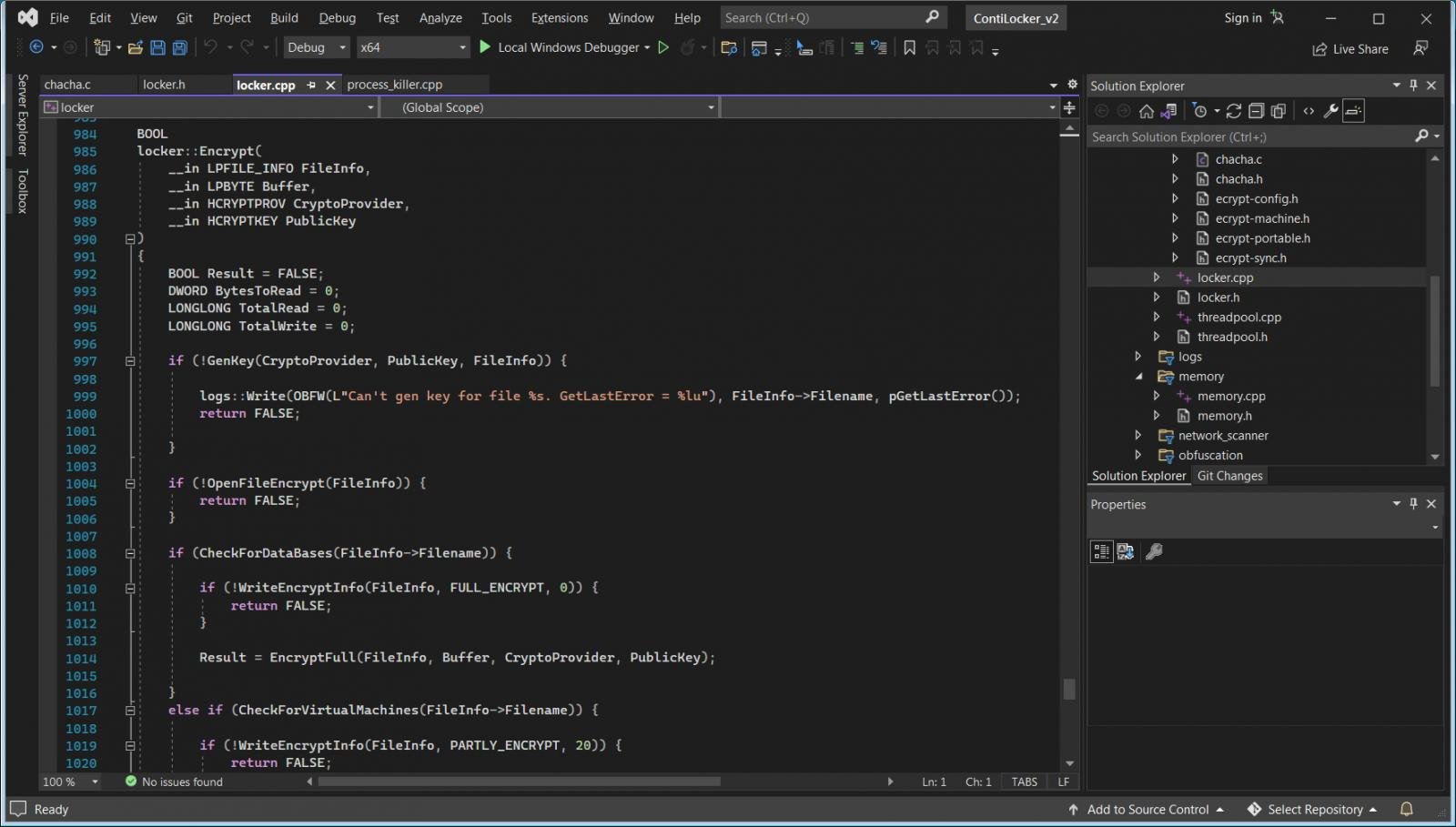
If you are a reverse engineer, the resource code could not supply added information. Nevertheless, the supply code supplies massive insight into how the malware performs for those who can program in C, but not necessarily reverse engineer.
Though this is good for protection investigation, the community availability of this code does have its negatives.
As we observed when the HiddenTear (for “academic factors”) and Babuk ransomware supply code was produced, risk actors speedily coopt the code to launch their very own operations.
With code as tight and clean as the Conti ransomware procedure, we need to count on other danger actors to try to start their possess felony operations employing the leaked supply code.
What might be additional practical, while, is the BazarBackdoor APIs and TrickBot command and command server supply code that was introduced, as there is no way to access that details without obtaining obtain to the threat actor’s infrastructure.
As for Conti, we will have to wait around and see if this “info breach” has much of an effects on their operation.
This has been a sizeable reputational blow for the team that may induce affiliate marketers to shift to yet another ransomware operation.
But, just like all businesses, and there is no denying Conti is operate like a business, knowledge breaches come about all the time.
